In today’s digital world, web application security is more critical than ever. With the increasing number of cyberattacks, organizations must ensure their applications are secure before deployment. OWASP ZAP (Zed Attack Proxy) stands out as one of the most trusted and user-friendly tools for identifying vulnerabilities in web applications. Developed by the Open Web Application Security Project (OWASP), this open-source tool enables developers, QA testers, and security professionals to conduct comprehensive penetration testing.
This guide provides a comprehensive overview of OWASP ZAP, covering installation and configuration, scanning techniques, and report generation. Whether you are a beginner exploring web security or an experienced tester looking to automate vulnerability detection, this guide will help you effectively use OWASP ZAP to strengthen your web application’s security posture.
Table of Contents:
- What is OWASP ZAP?
- Features of OWASP ZAP
- OWASP ZAP: Installation and Initial Configuration
- ZAP Desktop UI
- Mode of OWASP ZAP
- Running a Manual/Automated UI
- Generate ZAP Report
- How can OWASP ZAP be used for Web Application Security Testing?
- Conclusion
What is OWASP ZAP?
OWASP ZAP (Zed Attack Proxy) is a free, open-source penetration testing tool developed under the umbrella of the OWASP (Open Web Application Security Project). It is designed specifically for testing web applications and is widely used by security professionals, QA engineers, and developers.
The tool is flexible, extensible, and beginner-friendly, making it one of the most popular solutions for web security testing. Whether you are just starting with security testing or you’re an advanced tester, OWASP ZAP provides everything you need to find vulnerabilities and strengthen your applications.
Features of OWASP ZAP
- Works on all platforms (Windows, Mac, Linux, Docker)
- Easy to install and start using.
- Beginner-friendly interface, yet powerful for experts.
- Can run silently in the background for automation.
- Extendable with free add-ons.
- Free tool for more powerful execution
Installation and Initial Configuration
Prerequisites
- ZAP has installers for Windows, Linux, and Mac OS/X, as well as Docker images.
- Java Requirement
- OWASP ZAP is built in Java, so it requires Java 8 or later to run.
- Check your Java version:
- java -version
- If not installed, download from Oracle Java or use OpenJDK.
Note:
- On macOS, the installer already includes Java.
- On Windows/Linux, you must install Java separately.
- On Docker, Java is pre-packaged inside the container.
- Operating System
- ZAP supports Windows, Linux, macOS, and Docker.
- Recommended RAM: 4 GB or higher for smooth scanning.
- Browser
- Install a modern browser (Chrome/Firefox/Edge).
- You may need to configure it with ZAP’s proxy settings for intercepting traffic.
Step 1: Download OWASP ZAP
- Visit the official ZAP website: https://www.zaproxy.org/download/
- Choose the installer based on your OS:
- Windows: .exe installer
- macOS: .dmg package
- Linux: .tar.gz or .deb package
- Docker: Use the official Docker image owasp/zap2docker-stable
Step 2: Install OWASP ZAP
- Windows:
- Run the .exe installer.
- Follow the wizard (Next → Accept License → Install).
- After installation, launch ZAP from the Start Menu.
- macOS:
- Open the .dmg file.
- Drag ZAP into the Applications folder.
- Launch ZAP from Applications.
- Linux:
- Extract .tar.gz into a folder.
- Navigate to the folder and run:
./zap.sh - Or install .deb package via:
sudo dpkg -i zap-x.y.z.deb
Step 3: First Launch & Initial Configuration
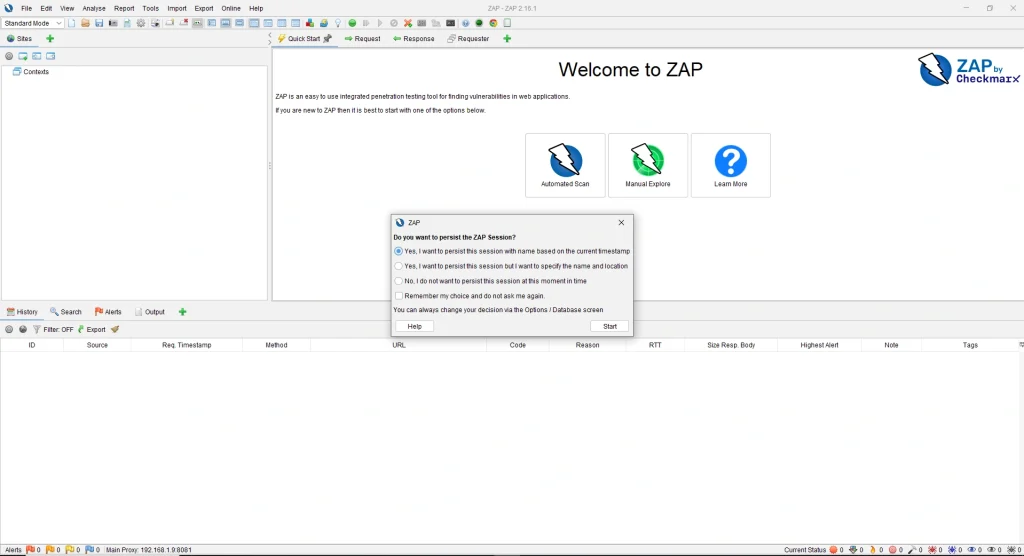
- Start ZAP → You’ll be asked about Session Persistence:
- Persist Session – Saves session data (choose this if you want to analyze results later).
- Do Not Persist – Data is temporary and will be lost on exit.
- For beginners, select “Do Not Persist” and click Start.
- Install ZAP Root CA Certificate (for HTTPS traffic interception):
- Open Tools → Options → Network → Certificates.
- Click Generate to create a root certificate.
- Export the certificate and import it into your browser (as a trusted authority).
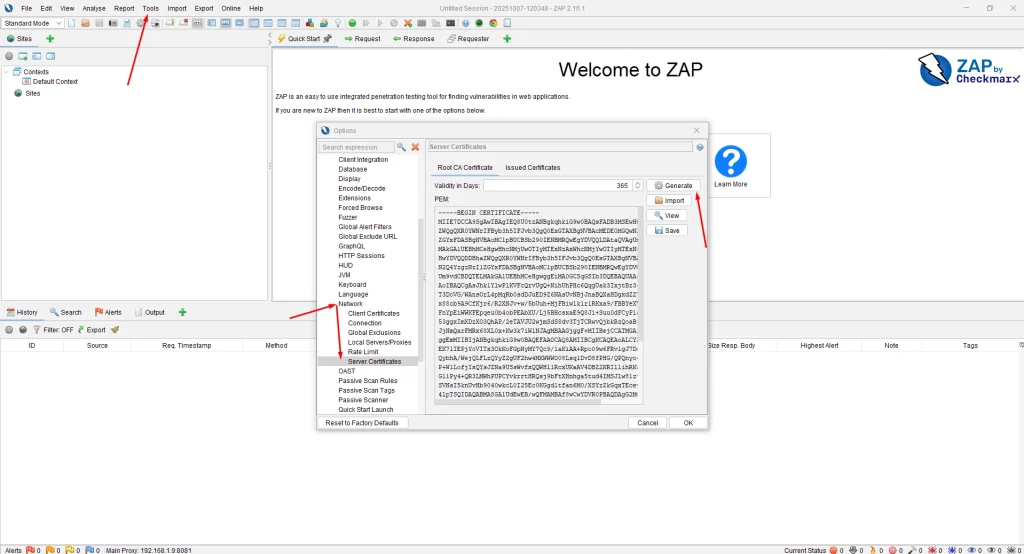
- This step is essential for capturing HTTPS traffic.
- Configure Browser Proxy
- Set browser proxy to:
- Address: localhost
- Port: 8080 (default)
- Now, all traffic will pass through ZAP for analysis.
- Set browser proxy to:

ZAP Desktop UI
The ZAP Desktop UI is composed of the following elements:
1. Menu Bar – Provides access to many automated and manual tools.
2. Toolbar – Includes buttons that provide easy access to the most commonly used features in ZAP.
3. Tree Window – Displays the Sites tree and the Scripts tree from left side view.
4. Workspace Window – Displays requests, responses, and scripts, and allows you to edit them for two options.
5. Information Window – Displays details of the automated and manual tools from the information.
6. Footer – Displays a summary of the alerts found and the status of the main automated tools for current scans.
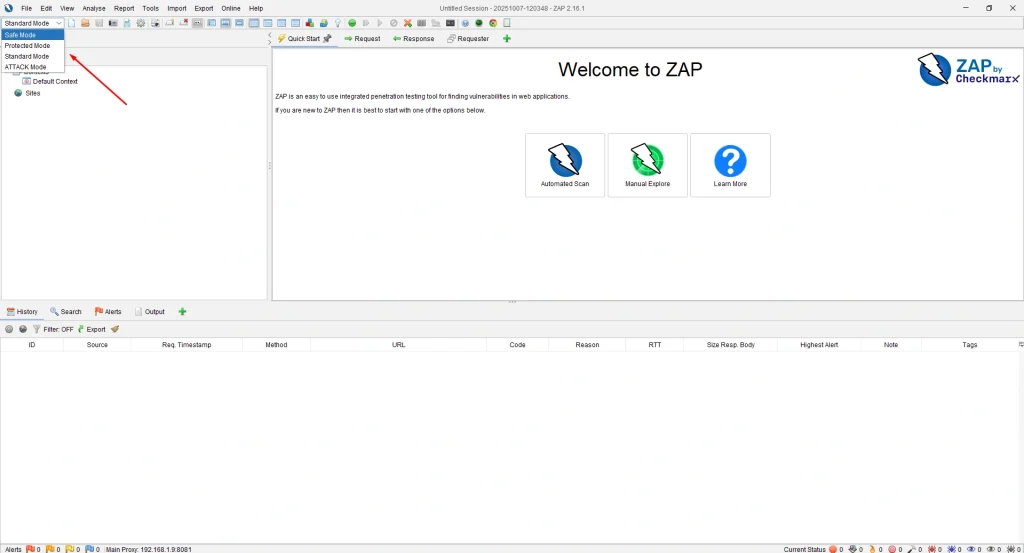
OWASP ZAP Mode:
OWASP ZAP provides four operational modes, each designed for different levels of testing:
1. Safe Mode – No potentially dangerous actions are allowed.
2. Protected Mode – Potentially risky actions are allowed only for URLs within scope.
3. Standard Mode – Full control; allows all actions (default mode).
4. Attack Mode – Any new nodes in scope are automatically scanned as soon as they are discovered.
Running a Manual/Automated UI
One of the easiest ways to start with ZAP is to perform a Quick Start Automated Scan:
Step 1: Launch ZAP and open the Quick Start tab.
Step 2: Click the Automated Scan button.
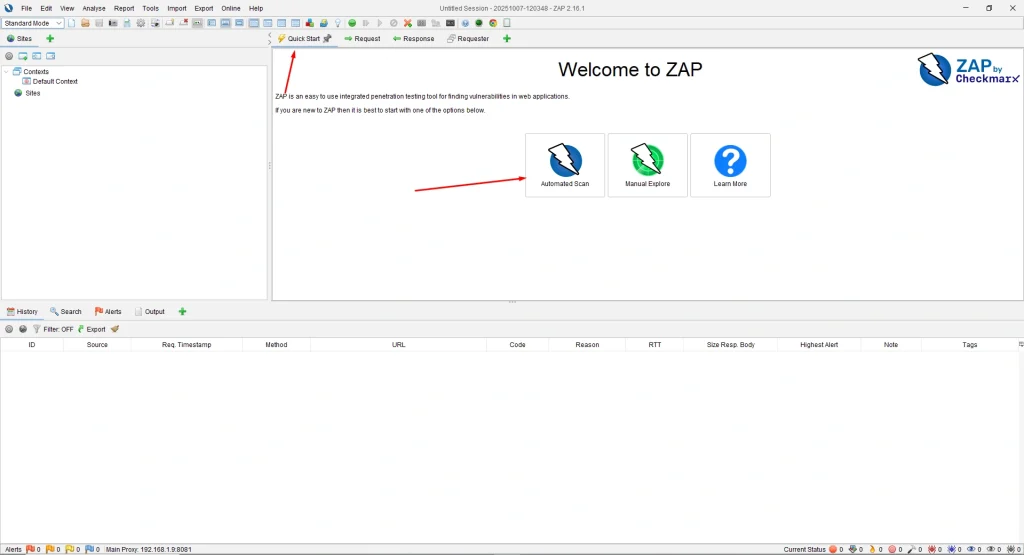
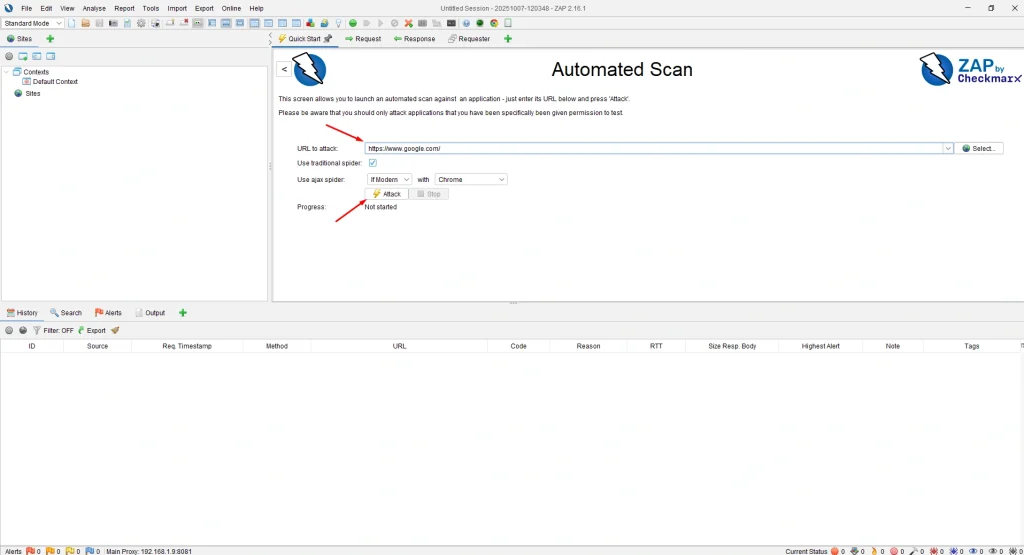
Step 3: Enter the URL of the target web application.
Step 4: Click Attack to start scanning.
Step 5: ZAP will perform a Spider Scan → AJAX Spider → Active Scan sequence.
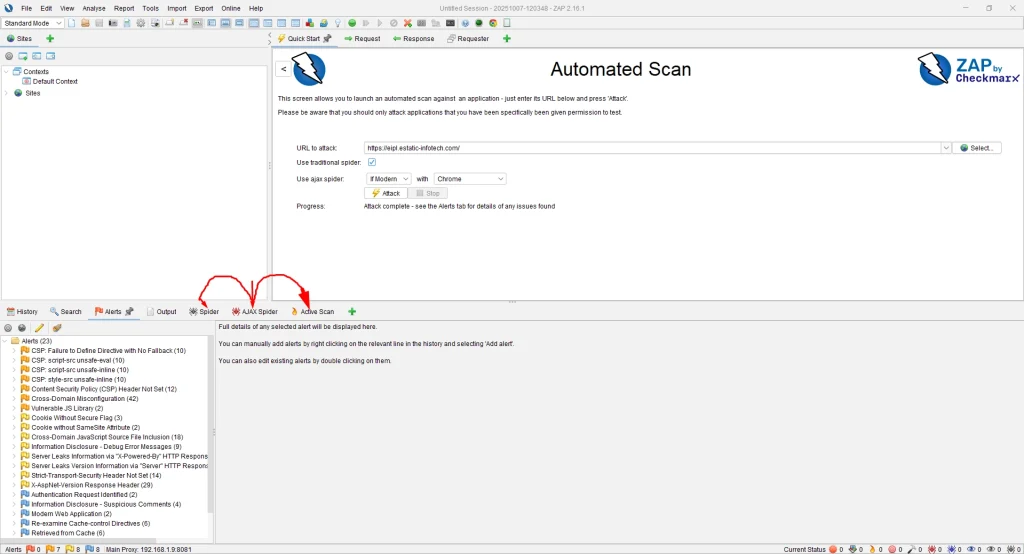
Within a few minutes, you’ll have a list of potential vulnerabilities in the target application.
Generating a Security Report in ZAP
ZAP makes it easy to generate detailed reports after a scan:
1. From the Menu Bar, select Report → Generate Report.
2. Choose the desired report directory.
3. Click Generate Report.
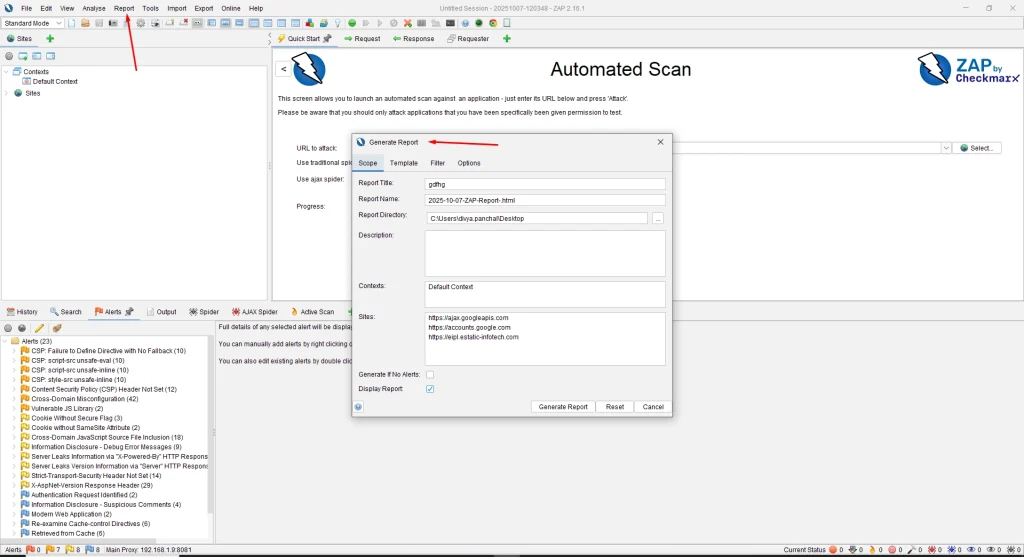
4. The report will be available in HTML format (can also be exported as PDF).
Exporting to PDF:
– Press CTRL + P (or Print option).
– Select Microsoft Print to PDF as the destination.
– Enable “Background graphics” if needed, then click Print.

How can OWASP ZAP be used for Web Application Security Testing?
OWASP ZAP is a free tool used by security professionals, developers, and testers to find and fix web application vulnerabilities. It helps in:
- Identifying vulnerabilities: Detects issues like SQL Injection, XSS, and insecure configurations.
- Validating security controls: Test input validation and access control mechanisms.
- Automating testing: Supports scripting to automate security checks.
- Integration: Works with tools like Jenkins and Burp Suite for CI/CD security.
- Active & passive scanning: Analyzes web app behavior to uncover hidden flaws.
- Fuzz testing: Sends unexpected inputs to find input handling weaknesses.
Conclusion
Its user-friendly interface, flexible modes, and automation capabilities make it suitable for both beginners and experts. By integrating ZAP into your testing workflow or CI/CD pipeline, you can proactively identify security risks such as XSS, SQL injection, and misconfigurations before they become real threats. To ensure web application security isn’t optional—it’s a necessity. Tools like OWASP ZAP empower teams to build safer applications, protect sensitive user data, and maintain trust in their digital ecosystems.


